762 days ago
Types of zero-knowledge proofs explained
Beyond the Basics: zkSNARKs vs. zkSTARKs
 Zero Knowledge Proofs (ZKP) are cryptographic protocols that allow one party (the Prover) to prove to another party (the Verifier) that a given statement is true without revealing any additional information beyond the validity of the statement itself. For more information on Zero Knowledge Proofs, check out our ultimate beginners’ guide here.
Zero Knowledge Proofs (ZKP) are cryptographic protocols that allow one party (the Prover) to prove to another party (the Verifier) that a given statement is true without revealing any additional information beyond the validity of the statement itself. For more information on Zero Knowledge Proofs, check out our ultimate beginners’ guide here.
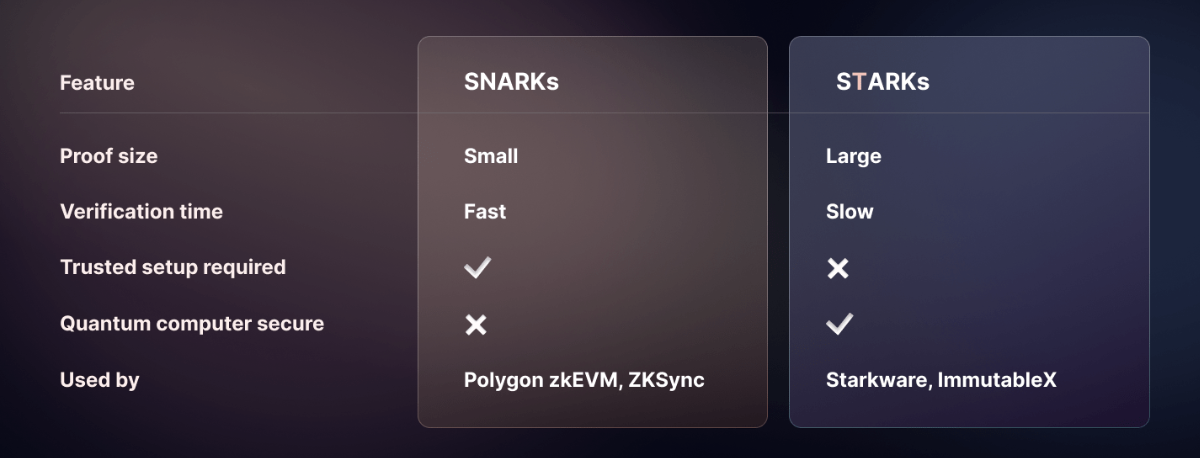
There are two main types of ZKP: STARKs (Scalable Transparent Arguments of Knowledge) and SNARKs (Succinct Non-interactive Arguments of Knowledge). Both types use complex mathematical algorithms to enable the Prover to prove the truth of a statement without revealing any additional information to the Verifier.
ZK SNARK
zkSNARKs, which stands for Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge, are cryptographic proof systems that allow a prover to convince a verifier that a statement is true, without revealing any information about the statement itself, besides the fact that it is true.
zkSNARKs encompass four key components, let’s discuss them with the following example:
Alice wants to prove to Bob that she knows the square root of 16 without revealing the actual square root.
-
Alice encodes the problem as an equation: x^2 - 16 = 0. The equation is true only if Alice knows the correct value of x (which is 4, the square root of 16)
-
Bob chooses a secret and calls it 's'. Alice proves the equation holds true at 's' without revealing x. This simplifies the problem and reduces the information needed for verification
-
Alice and Bob use a secret language (encryption) that allows them to work with the problem without revealing x. This lets them do maths with hidden numbers, so Alice can show Bob that the equation works with x in the secret language
-
Alice hides the encrypted values by multiplying them with random numbers. This prevents Bob from learning the actual square root, but he can still check that the original equation holds true.
ZK SNARK also uses a trusted setup process to generate certain cryptographic keys or parameters needed for the system to work properly.In context to above example let’s say to set up this game, Alice and Bob need to make some special rules. They both invite some people they trust to help them make the rules. These people work together to make some secret codes that Alice and Bob can use in the game. Once they have the codes, Alice can prove to Bob that she knows the square root of 16 without telling him what it is.
As this involves multiple contributors giving random pieces of information to create the parameters, ensuring no one knows the complete set. However, if the setup is compromised, the entire system may be compromised as well.
Now let’s break down each part to understand ZK SNARKs more clearly Zero Knowledge allows the prover to prove the validity of a statement to the verifier without disclosing any additional information.
Succinct means that the proof is very short and can be checked very quickly by verifier. Non-Interactive means the prover and verifier only need to interact once to prove the statement.
Argument:The prover generates a zk-SNARK proof to demonstrate knowledge of a statement, which satisfies the soundness requirement. This ensures it's almost impossible for attackers to produce a false proof accepted as valid by the verifier.
(Of) Knowledge: The prover convinces the verifier that they possess some secret information without revealing what it is. The prover can generate a zero-knowledge proof only if they have access to the secret.
ZK STARK
This stands for Zero-Knowledge Scalable Transparent Argument of Knowledge and is a more recent variant of the zk-SNARK protocol.
zk-STARKs don't rely on trusted setups. Instead, they use publicly available randomness to set up the parameters needed to generate and verify their proofs. This means that ZK-STARKs are more transparent and don't require any trust in specific individuals or parties to generate their proofs.
They have two major advantages: Scalability: ZK-STARKs can handle very large computations with minimal overhead, and do not require a trusted setup phase,
Transparency: ZK-STARKs are more transparent because they use a way of generating important information that anyone can verify, instead of relying on a group of people to generate it together.
Conclusion
 In conclusion, Zero Knowledge Proofs, including STARKs and SNARKs, are powerful tools for enhancing privacy and security in various industries.
In conclusion, Zero Knowledge Proofs, including STARKs and SNARKs, are powerful tools for enhancing privacy and security in various industries.
They allow for the validation of information without the need to disclose additional details beyond the validity of the statement, making them an important solution for protecting sensitive information. As the adoption of blockchain technology and decentralized systems continues to grow, Zero Knowledge Proofs are poised to play an even more significant role in the future.
About Gelato
Gelato is a Web3 Cloud Platform empowering developers to create automated, gasless, and off-chain-aware Layer 2 chains and smart contracts. Over 400 web3 projects rely on Gelato for years to facilitate millions of transactions in DeFi, NFTs, and gaming.
-
Gelato RaaS: Deploy your own tailor-made ZK or OP L2 chains in a single click with native Account Abstraction and all Gelato middleware baked in.
-
Web3 Functions: Connect your smart contracts to off-chain data & computation by running decentralized cloud functions.
-
Automate: Automate your smart contracts by executing transactions automatically in a reliable, developer-friendly & decentralized manner.
-
Relay: Give your users access to reliable, robust, and scalable gasless transactions via a simple-to-use API.
-
Account Abstraction SDK: Gelato has partnered with Safe, to build a fully-fledged Account Abstraction SDK, combining Gelato's industry's best gasless transaction capabilities, with the industry's most secure smart contract wallet.
Subscribe to our newsletter and turn on your Twitter notifications to get the most recent updates about the Gelato ecosystem! If you are interested in being part of the Gelato team and building the future of the Internet browse the open positions and apply here.

